Driving privacy-preserving computing technologies – Bosch has joined the MPC Alliance
Bosch Research Blog | Post by Sven Trieflinger, 2021-01-27

Data is a mixed blessing
Data is considered the new oil fueling today’s economies. If that is the case, the ability to leverage data will be a prerequisite for lasting success in our data-driven economy. Owning data, however, is a mixed blessing – it comes with significant challenges with respect to security and privacy.

Building trust and preventing data breaches are not the only challenges. In 2018, the General Data Protection Regulation became effective and has been protecting the personal data and privacy of EU citizens ever since. This milestone marked the beginning of a global trend in the free world economy towards stricter legislation. Similar regulations have already or will become effective in the US (CCPA), in Brazil (LGPD), India (PDPB), Japan (APPI) and Australia (PAPA), to name the most important ones. Operating at a global scale in this setting is getting increasingly challenging and will require the adoption of cross-regulatory compliance strategies.
Note that these regulations are no mere paper tigers: The GDPR, for example, imposes severe penalties of up to 4% of annual sales in case of violation. Conflicts between the GDPR and laws in other jurisdictions are consequently addressed as well: The “Schrems II” decision of the European Court of Justice in July 2020 has placed the use of non-EU IT infrastructure for the processing of personal data of EU citizens under significant legal risks.
While Bruce Schneier, a renowned security expert, mainly had data theft in mind when he coined the phrase “data is a toxic asset,” I think it describes the other challenges of owning data equally well.
Privacy-preserving computing technologies on the rise
I think that these challenges can be tackled only by a combination of organizational and technological measures. Privacy-preserving computing technologies (PPCTs) are one very important example of the latter. PPCTs are a family of cybersecurity techniques that look at how to represent data in a form that can be shared, analyzed and operated on without exposing the raw information. At Bosch Research, we started looking at PPCTs several years ago already and quickly understood their huge potential. Recently, the key role of PPCTs in tackling the security and privacy issues arising in our data-driven economy have also been recognized by companies such as Gartner or Accenture.
- “Gartner believes that by 2025, half of large organizations will implement privacy-enhancing computation for processing data in untrusted environments and multiparty data analytics use cases.” (Gartner)
- “With the growing argument for ecosystem collaboration and the need for effective and secure methods of data exchange and collaboration, PPC techniques and their successors will be critical to effective, safe and secure data sharing.” (Accenture)
The PPCT toolbelt
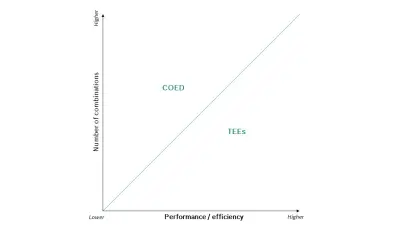
The term privacy-preserving computing technology refers to a wide range of technologies. Those we see the most potential in as of today are Trusted Execution Environments (TEEs), Computing on Encrypted Data (COED) methods and Statistical Disclosure Control (SDC) technologies.
What are...
TEEs are tightly controlled execution environments that allow for data processing within hardware-provided, encrypted private memory areas directly on the microprocessor chip. They are characterized by low efficiency and performance losses compared to unprotected processing. TEEs are available today from various vendors including Intel (Software Guard Extensions), AMD (Secure Encrypted Virtualization) and ARM (TrustZone).
COEDs are cryptographic software-based methods that enable computation on encrypted data without the need to decrypt it. The most prominent COED methods are secure multi-party computation and homomorphic encryption. When compared to TEEs, COEDs have the advantage of being provably secure, but typically incur much higher overheads. As of today, COED products are available mainly from startups with various levels of maturity.
SDC techniques allow broad statistical information to be gathered and inferred from data without the actual specifics of individual data items being exposed. While TEEs and COEDs keep data protected during processing, SDC techniques become important when the results of a computation leave the protected parts of a system.
Introducing PPCTs in an industrial context
Our mission is to make PPCTs available to our business units as a tool to deliver business value.
At Bosch Research, our mission is to make PPCTs available to our business units as a tool to deliver business value. Depending on the specifics of the concrete use case, we select the best-fitting tools from the PPCT toolbox in order to lower the security and privacy risks as much as we can without violating performance and efficiency requirements.
For the class of use cases where security and privacy are key requirements, but performance and efficiency requirements are low to moderate, secure multi-party computation (MPC) plays an important role.
The basic idea of MPC is to split sensitive data into so-called secret shares. The shares do not reveal any information about the secret as long as they are not recombined. Each party participating in a computation receives one of the shares and then uses basic MPC protocols for addition and multiplication without gaining insight into the inputs or outputs of these operations. By combining these simple protocols into more complex ones, an MPC-based processing architecture becomes Turing-complete. This roughly means that you can do everything with it that can be done on a Von Neumann architecture.
One of our concrete use cases where MPC shines is privacy-preserving energy trading amongst households. The need for protecting the privacy of residents in combination with a comparatively low computational complexity makes this use case perfect for MPC. Read more about this use case on the Bosch Economy of Things Blog.
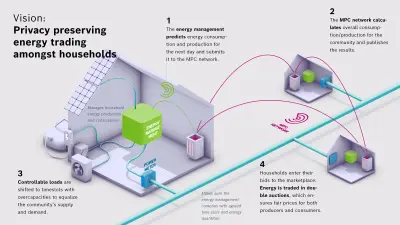
Privacy-preserving energy trading is only one example of a myriad of potential use cases that Bosch as an AIoT company can address with PPCTs in general and with MPC in particular. More information on additional use cases can be found in our success story on Trustworthy Computing.
Moving forward with allies
In order to be able to closely follow future developments in the area of industrial application of secure multi-party computation, to influence upcoming standardization in our interest, and to promote our own activities, Bosch joined the MPC Alliance in December 2020 on the initiative of Bosch Research.
The MPC Alliance is a group of nearly 40 companies of all sizes, from highly innovative startups to global players like Salesforce or Alibaba Group, with the shared mission to accelerate the adoption of MPC technology.

As Bosch Research, we will start several initiatives in the coming months to bring forward the idea of using PPCTs in an industrial setting in close collaboration with partners.
I think, the future of PPCTs will be an exciting one – at Bosch and throughout the industry. Stay tuned!
What are your thoughts on this topic?
Please feel free to share them or to contact me directly.
Author: Sven Trieflinger
Sven is a Research Engineer and Senior Project Manager at Bosch Research. He received his doctoral degree from the Institute for Parallel and Distributed Systems at the University of Stuttgart in 2011 for his work on Peer-to-Peer Grid Computing for Irregularly Structured Problems. His scientific expertise is in distributed systems, cloud technologies and scientific computing. He has over 15 years of experience in the design, architecture and implementation of distributed systems and cloud platforms. Sven holds several patents in the area of theory and applications of privacy-preserving computing technologies. As a Senior Project Manager, he can draw on eight years of experience in managing international research projects.




